Contents
 Eva Iyeke
Solutions Engineer – Africa at MetaMap
Eva Iyeke
Solutions Engineer – Africa at MetaMap  Ani Ntia
Product & Growth Marketing Manager – Africa at MetaMap
Ani Ntia
Product & Growth Marketing Manager – Africa at MetaMap Techniques to Mitigate Identity Theft in Your Operations
Identity theft and digital fraud are a constant danger to both your company and your end-users. Therefore, it’s crucial to take proactive measures capable of evolving at the pace of criminals to protect your daily operations and your company’s expansion plans. But what are these measures?
To answer this and many other questions, our experts, Eva Iyeke – Solution Engineer – Africa, and Ani Ntia – Product Marketing & Growth Manager – Africa at MetaMap, shared the screen in our most recent free webinar to review a wide variety of topics, such as:
- How secure is your business?
- New criminal trends in identity theft.
- Real-life fraud cases and how to prevent them.
- How major companies are defeating digital fraud.
How Secure is Your Business?
Although it may sound intuitive, our experts mentioned on our MetaChat that before protecting your business against new trends in identity theft and digital fraud, you must first evaluate the current security measures of your operations.
What to take into account?
- Do you have strong password policies?
- Are your employees trained in best cybersecurity practices?
- Are you using adequate encryption to protect sensitive data?
- What is your current non-compliance risk?
- Do you have the proper tools to fight against current and future fraud attempts?
- Does your company need an ally to mitigate the risk of phishing and other fraud attempts?
“At the end of the day, there are only two types of companies, those that have been attacked in the past and those that will be attacked in the future. Are you prepared?”
This makes that one of the best first actions to take is to evaluate your current security measures, identify possible gaps and immediate needs, and draft a plan to improve the security of your operation, for the present and the future.
Do you want to see more videos and blog posts on topics like KYC, AML, or Digital Banking? Access our Webinar-Hub. (This could be a banner).
New Criminal Trends in Identity Theft
Cybercriminals are constantly evolving their tactics, which means that companies in all industries must be aware of the latest trends to protect themselves against multiple digital fraud attempts.
One of the biggest trends of recent times is social engineering techniques, such as phishing attacks, which can trick employees into giving sensitive information, such as login keys or credentials, to criminals.
Another new criminal trend is synthetic identity, where criminals create new identities by combining real and false information from ordinary people. This makes it difficult for manual identity verification methods to detect fraud attempts in the onboarding process.
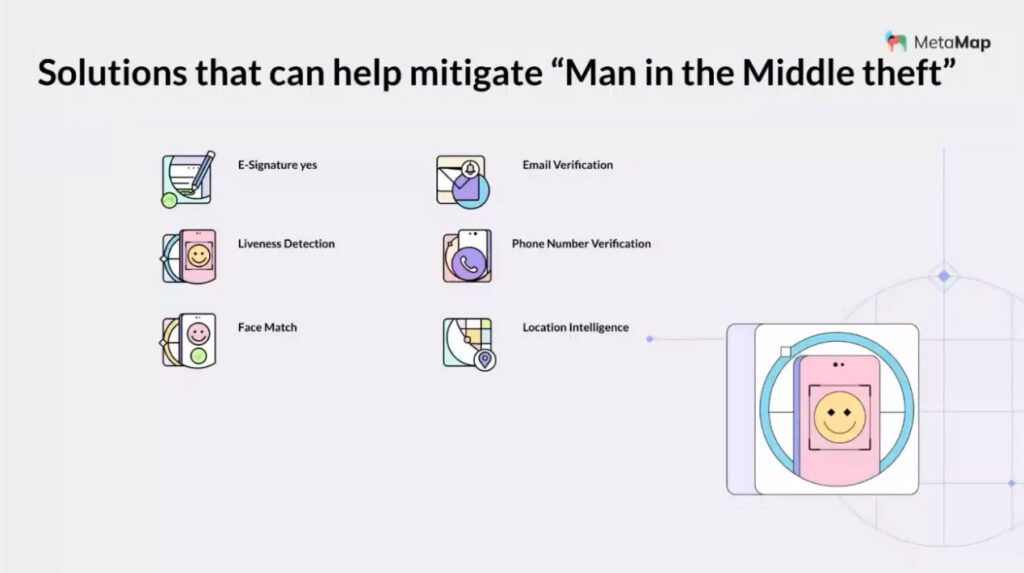
Along with this, a Man-In-The-Middle (MITM) attack occurs when a hacker intercepts communication between two parties, giving them access to information they would not usually have.
The attacker can then manipulate the communication channel without either party realizing it. This can lead to the theft of sensitive information, such as login credentials or financial data.
To combat these trends, your organization must remain vigilant, regularly monitor their accounts for suspicious activities, and use multifactor authentication, biometric technology, and other security measures to protect your users and business platforms.
“If, for example, you implement several layers to enter your system, either for your workers or your users, such as biometric verification, email verification, and a GPS and IP verification. You will significantly increase the cost that criminals have to bear to attack you and exponentially reduce fraud risks”
Real Fraud Cases and What to Learn from Them
Examining real fraud cases will not only allow you to discover the implications and consequences -monetary, legal, and/or reputational- that actual companies had when facing any of these attacks that our experts have mentioned.
But also, you will be able to take a sneak peek beyond the concepts and focus on the techniques and tactics that criminals use to bypass security barriers. These insights will help you strengthen your defenses and prevent similar attacks in the future.
For example, let’s reference the Equifax hack in 2017. They compromised the personal information of over 143 million people. This hack occurred due to a small but exploitable vulnerability where hackers could obtain both employees’ and end-users private information.
But that failed on the Equifax systems.
– The hackers obtained the private keys of various users and staff on a secondary company website. It is believed that through an attack on Man-In-The-Middle (MITM), they could read the usernames and passwords of end users and workers.
A quick solution: Not only using a usernames and a passwords to access to your platform, if not as well another method, like biometric authentication or a 2FA token.
-The lack of proper Admin Management Systems. Allowing attackers to obtain usernames and passwords stored in plain text. With this information, they were then able to gain access to additional systems and finally get hold of sensitive data from 143 million people.
A quick solution: Implement layered access control within your platform. Where, for example, someone from the marketing team does not have direct access to the servers. If a hacker manages to get hold of your workers’ credentials, they cannot attack the rest of your company.
As Eva Iyeke and Ani Ntia mentioned on our free webinar, the way to go is to use different layers of security, such as biometric authentication, liveness detection validation, and location intelligence, which includes GPS, IP data, and Proxy and VPN blockers.
These mentioned security layers would help you to be protected against fraud attempts by detecting any possible unauthorized access from an unusual location, or for a hacker.
How Leading Companies Are Doing It
Large companies worldwide are adopting various measures to enhance their security, for example:
Zero trust approach: This relies on data and validation systems to grant access rather than personal trust.
Implementation of a user or admin management system: This allows for the precise management of staff or client access credentials.
Multiple security layers: Such as biometric data or intelligence location, add an extra level of protection to platforms, making it more challenging for attackers to access critical areas even if they obtain login information.
“By combining these techniques, companies are detecting identity theft more effectively. In addition, larger companies are investing in service providers and training and educating employees to ensure everyone in the organization knows the risks and best cybersecurity practices”.
MetaMap, an Ally in the Fight Against Digital Fraud.
During our latest MetaChat, hosted by our experts, Eva Iyeke – Solution Engineer – Africa, and Ani Ntia – Product Marketing & Growth Manager – Africa at MetaMap, our audience learned that the best way to protect the safety of their users and data is by using different layers of security, both in the onboarding process of new users and for accessing your platforms.
However, we know firsthand that the high logistical and monetary cost of developing all these in-house security systems or, alternatively, hiring different validation services from various companies can become a barrier to expanding into new markets and reaching more customers.
All to keep your company and users safe and compliant with national and international regulators.
Therefore, MetaMap offers a one-stop-shop for all your identity validation needs:
- AI-powered automatic onboarding: Onboard new customers in minutes, without friction, and completely secure.
- Liveness Detection: Fight identity fraud by requesting your new users to upload a video selfie to verify that they are real and that their biometric data matches their national identity documents.
- Phone and Email verifications: Request that your new users verify their phone number and email address, so you can determine if these accounts are flagged with any kind of risk.
- ID Document Verification Service: Validate that the identity document uploaded by your user has no alterations and compare it to official government sources, PEP lists, and more.
Through these identity validation tools and 25+, MetaMap allows your company to remove the burden of regulatory compliance and identity fraud concerns.
Meanwhile, you can focus on the untapped potential of your business and your users, accessing more customers and more markets.
For more information on how MetaMap can help your company to unlock this potential, contact us today, and one of our experts will answer all your questions.
Related content
- BLOG |
- 4 MIN
- BLOG |
- 5 MIN
- BLOG |
- 5 MIN
Subscribe to the newsletter and stay up to date with promotions, special offers and news